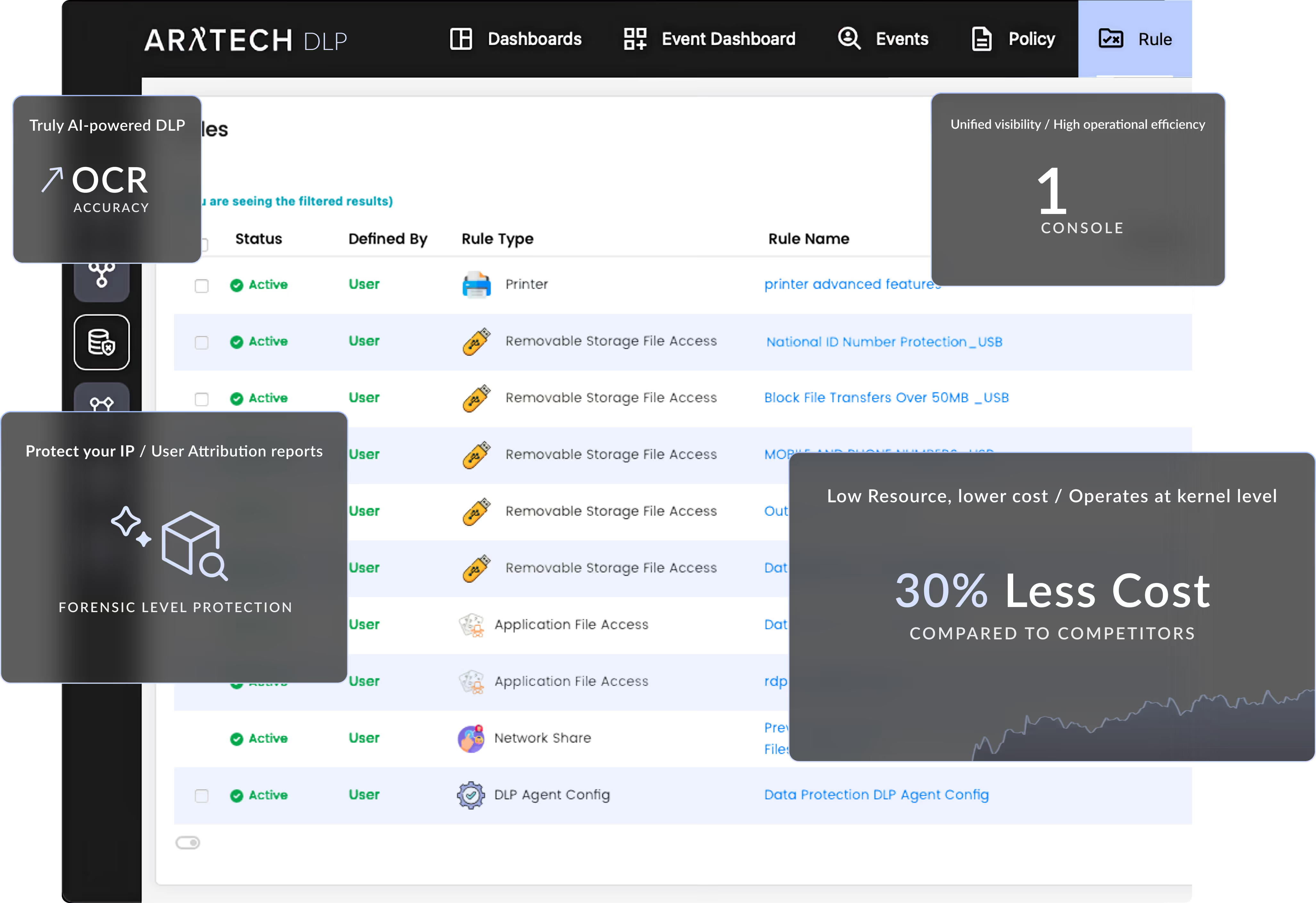
Eliminate the gaps left by legacy vendors. We use a kernel-level driver to secure the operating system deep below the application layer. Enforce unbypassable control over every channel to ensure your data never leaves.
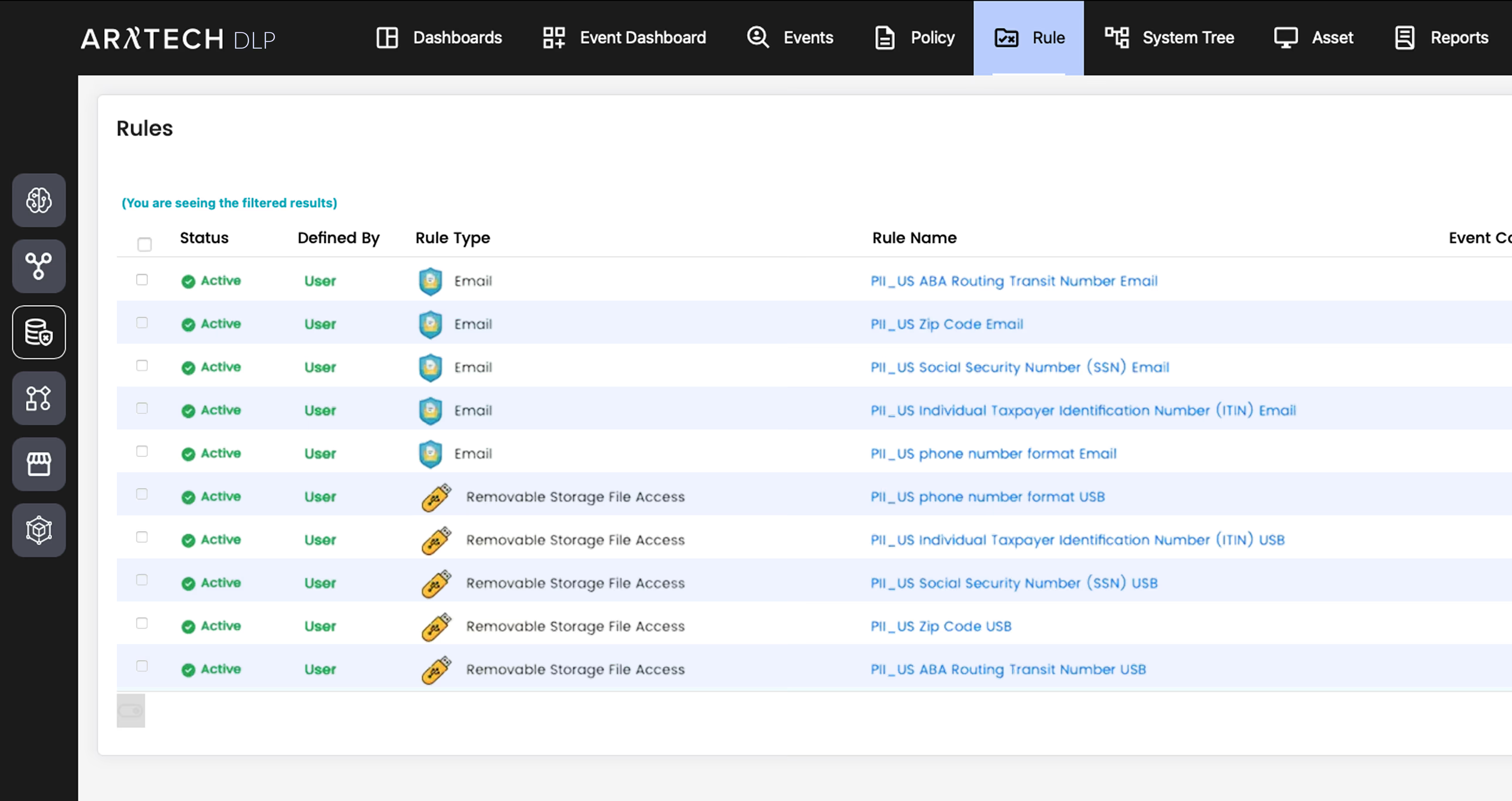
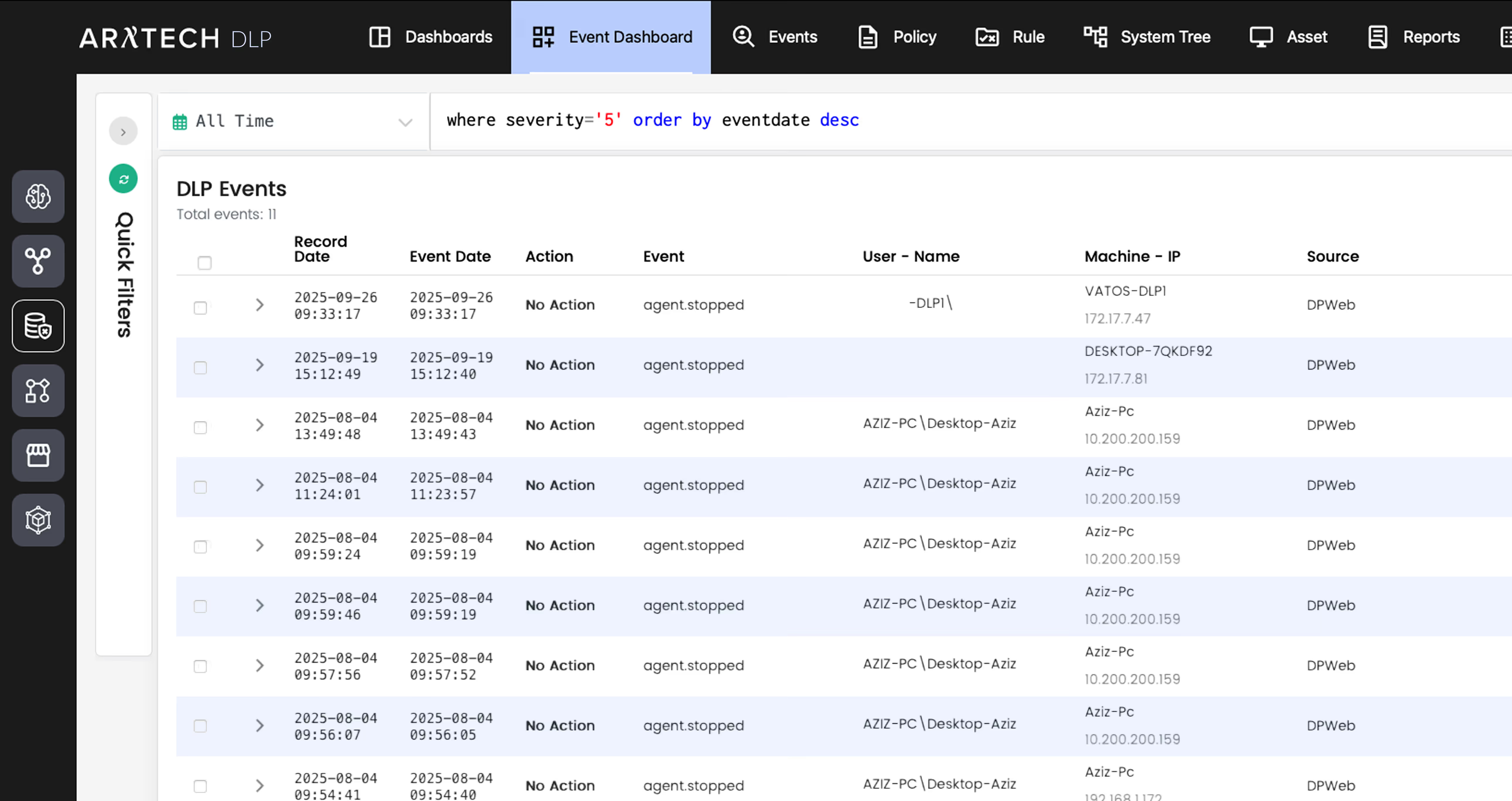
Move beyond passive alerting that arrives too late. We utilize a modern microservice architecture to inspect and block traffic at machine speed. Prevent exfiltration instantly to ensure business continuity without interruption.
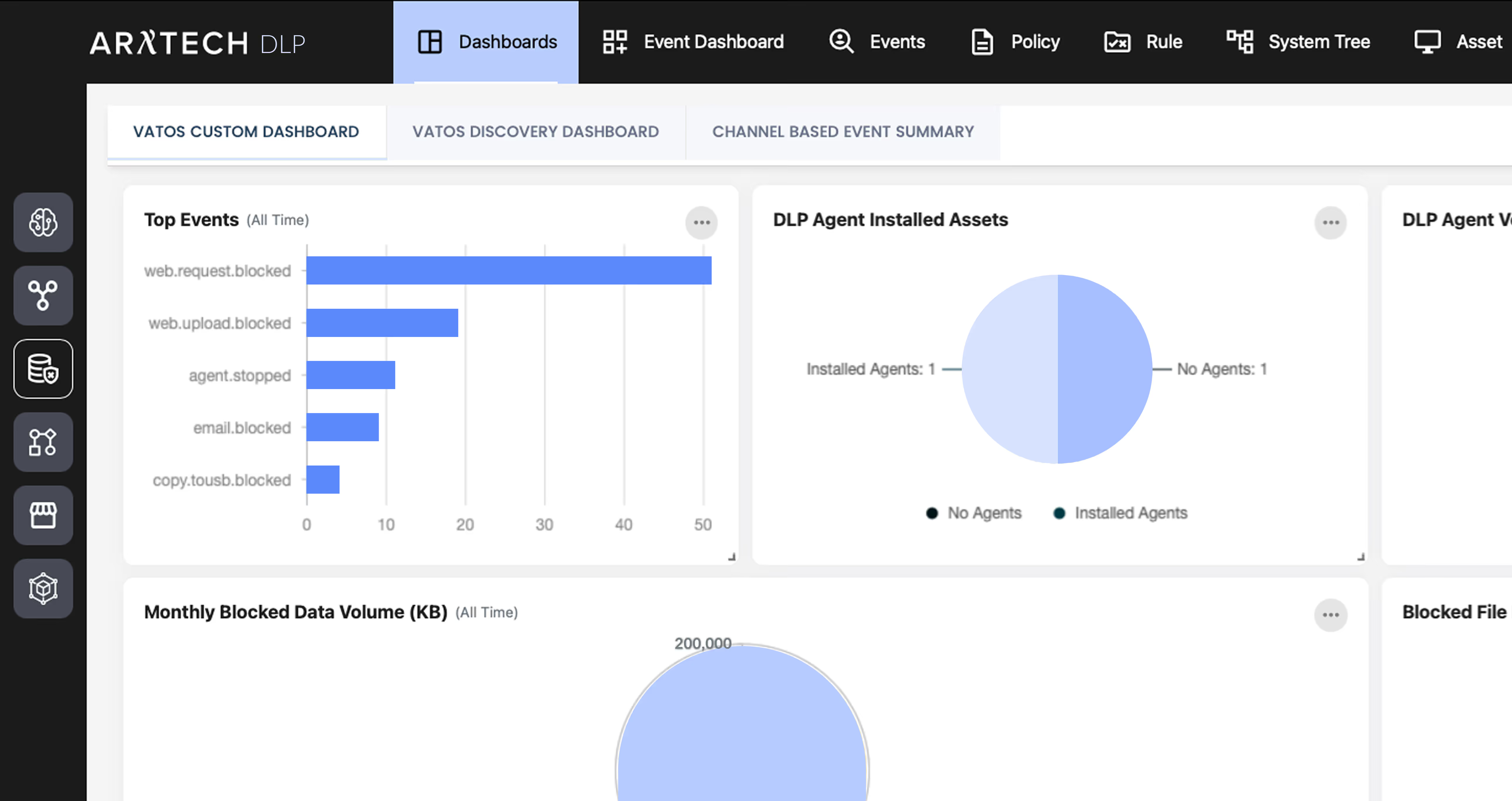
You cannot secure invisible threats. We map high-risk users and shadow IT across your infrastructure using dynamic visualization. Transform raw logs into clear executive intelligence that validates your security posture.
Secure your innovation without stalling productivity. We apply context-aware AI and proprietary OCR to read complex files like images and GenAI prompts. Detect actual theft with forensic accuracy while eliminating the noise that frustrates your team.